
TTool offers security, safety and performance for embedded systems
Carnot EN, Digital, In the NewsI’MTech is dedicating a series of articles to success stories from research partnerships supported by the Télécom & Société Numérique Carnot Institute (TSN), to which Télécom ParisTech belongs.
[divider style="normal" top="20"…

PAPAYA: a European project for a confidential data analysis platform
Digital, Europe EN, In the NewsEURECOM is coordinating the three-year European project, PAPAYA, launched on May 1st. Its mission: enable cloud services to process encrypted or anonymized data without having to access the unencrypted data. Melek Önen, a researcher specialized…
What is mechatronics?
Digital, In the News, Materials, What's?Intelligent products can perceive their environment, communicate, process information and act accordingly… Is this science fiction? No, it’s mechatronics! Every day, we come in contact with mechatronic systems, from reflex cameras to our…

Medcam: a high-quality image for laparoscopy
Digital, Health, In the News, Start-up-en300,000 laparoscopies are performed every year in France. At ten euros per minute spent in the operating room for procedures that last from one to ten hours, any time that can be saved is significant. Medcam helps save precious minutes by reducing…

Data-mobility or the art of modeling travel patterns
Digital, In the News, MobilityThe major rail workers’ strike in France on the spring of 2018 transformed French travel habits, especially in the Ile-de-France region. Vincent Gauthier, a researcher at Télécom SudParis, is working to understand the travel patterns in…
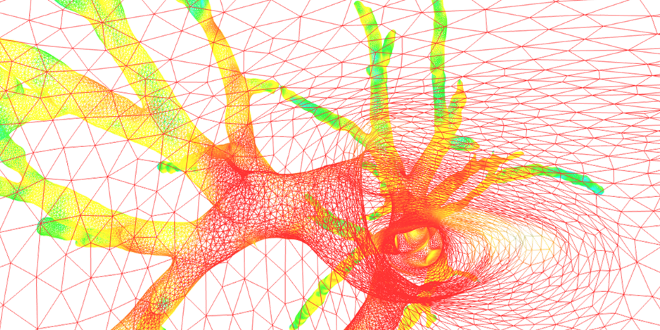
BioMICA platform: at the cutting edge of medical imaging
Carnot EN, Digital, Health, In the NewsAmong the research platforms at Télécom SudParis, BioMICA has developed bio-imaging applications that have already been approved by the medical field. Airways, its 3D representation software, received funding from Télécom & Société…

OMNI: transferring social sciences and humanities to the digital society
Carnot EN, Digital, In the News, SocietyI’MTech is dedicating a series of articles to success stories from research partnerships supported by the Télécom & Société Numérique Carnot Institute (TSN), to which IMT Atlantique belongs.
[divider style="normal" top="20" bottom="20"]
Technology…

GDPR: towards values and policies
Digital, In the News, SocietyOn May 25th, the GDPR came into effect. This new regulation requires administrations and companies in the 27 EU countries to comply with the law on the protection of personal data. Since its creation in 2013, the IMT Research Chair Values and…

Sociology and philosophy combine to offer a better understanding of the digital metamorphosis
Digital, In the News, SocietyIntellectual, professional, political, personal, private: every aspect of our lives is affected by technological developments that are transforming our society in a profound way. These changes raise specific challenges that require a connection…
Putting sound and images into words
Digital, Europe EN, In the NewsCan videos be turned into text? MeMAD, an H2020 European project launched in January 2018 and set to last three years, aims to do precisely that. While such an initiative may seem out of step with today's world, given the increasingly important…

