
BioDigital, a new technology to combat identity spoofing
Digital, In the NewsI’MTech is dedicating a series of articles to success stories from research partnerships supported by the Télécom & Société Numérique Carnot Institute (TSN), to which Télécom SudParis belongs. The original version of this article…
Pierre Comon: from the brain to space, searching for a single solution
Digital, In the News, PortraitPierre Comon’s research focuses on a subject that is as simple as it is complex: how to find a single solution to a problem. From environment to health and telecommunications, this researcher in information science at GIPSA-Lab is taking on…
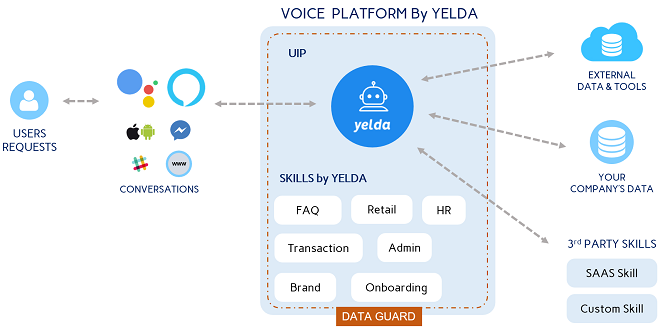
Yelda and OSO-AI: new start-ups receive honor loans
Digital, In the News, Start-up-enOn December 6, the Committee for the Digital Fund of the Graduate Schools and Universities Initiative chose two start-ups to receive honor loans: Yelda and OSO-AI. Together, Yelda, a start-up from the incubator IMT Starter, and OSO-AI, from…

How has digital technology changed migrants’ lives?
Digital, In the News, SocietyOver the past few decades, migrants have become increasingly connected, as have societies in both their home and host countries. The use of new technologies allows them to maintain ties with their home countries while helping them integrate…

Left out of the digital revolution?
Digital, In the News, SocietyDominique Pasquier, Télécom ParisTech, Institut Mines-Télécom (IMT)
This text is published as part of the "Digital Society" column written by researchers from the Economic and Social Sciences department at Télécom ParisTech, members…

What is the Industrial Internet of Things (IIoT)?
Digital, In the News, Industry, What's?Industry and civil society do not share the same expectations when it comes to connected objects. The Internet of Things (IoT) must therefore adapt to meet industrial demands. These specific adaptations have led to the emergence of a new field:…
What is digital simulation?
Digital, In the News, What's?Digital simulation has become an almost mandatory step in developing new products. But what does "simulating behavior" or "modeling an event" really mean? Marius Preda, a computer science researcher at Télécom SudParis, explains what's hiding…

AI in healthcare for the benefit of individuals and society?
Digital, Health, In the NewsArticle written by Christian Roux (Director of Research and Innovation at IMT), Patrick Duvaut (Director of Innovation at IMT), and Eric Vibert (professor at Université Paris-Sud/Université Paris Saclay, and surgeon at Hôpital Paul Brousse…

RAMSES: Time keeper for embedded systems
Carnot EN, Digital, In the NewsI’MTech is dedicating a series of articles to success stories from research partnerships supported by the Télécom & Société Numérique Carnot Institute (TSN), to which Télécom ParisTech belongs.
[divider style="normal" top="20"…

20 terms for understanding mobility
Digital, In the News, MobilityIncreasingly linked to digital technology, mobility is becoming more complex and diversified. Autonomous driving, multimodality, rebound effect and agile method are all terms used in the study of new forms of mobility. The Fondation Mines-Télécom…

