Posts
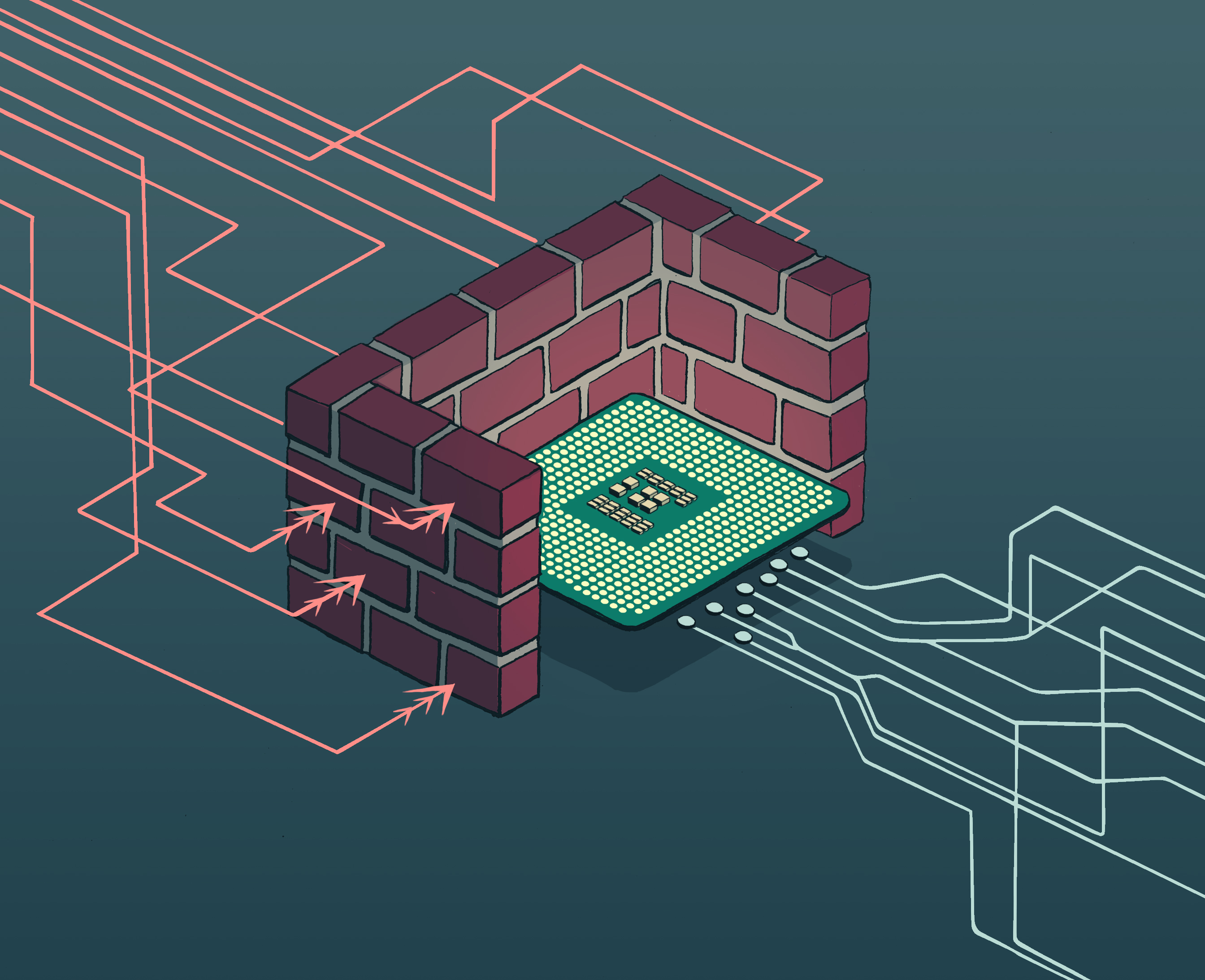
Using hardware to defend software against cyber-attacks
Digital, In the NewsSoftware applications are vulnerable to remote attacks via the internet or local networks and are cyber-attackers’ target of choice. While methods combining hardware and software have already been integrated into the most recent processors…

